Quick Summary
Secure your organization’s assets and users' sensitive information with threat detection and response systems. These systems can proactively identify and mitigate cybersecurity threats. Get your hands on this blog and explore its meaning, advantages, working, features, types of threats, best practices methods, challenges, and all that you need to know.
Data fuels innovation and connectivity drives progress whereas, in the interconnected world, these very pillars of growth also expose us to unprecedented risks. Cyber threats are persistent, evolving, and increasingly sophisticated.
Businesses today face the daunting challenge of protecting sensitive information which ensures operational continuity and maintains trust in an environment fraught with danger. This is where Threat Detection and Response (TDR) systems become indispensable.
Threat detection and response systems are sentinel cybersecurity systems that combine advanced technologies like artificial intelligence (AI), machine learning (ML), and real-time threat intelligence to anticipate, detect, and neutralize cyber threats.
From safeguarding against network intrusions and mitigating malware to defending against insider threats, these TDR systems act as a dynamic shield for businesses navigating the digital frontier.
In this article, you can embark on the journey of threat detection and response systems and its entire guide, from meaning to challenges to strategies to everything—all at your fingertips.
What You’ll Learn:
-
What are threat detection and response systems,
-
What are the advantages of threat detection and response solutions,
-
How do these threat detection and response solutions work,
-
What threats do these threat detection and response solutions detect and prevent,
-
What are the features of threat detection and response solutions,
-
What are the strategies to implement threat detection and response systems,
-
What are the common types of threat detection and response systems,
-
What are the methods of threat detection in TDR systems,
-
What are the challenges of threat detection and response solutions,
Understanding Threat Detection and Response Systems (TDR)
Threat detection and response systems are essentially helping organizations identify and mitigate malicious activities before they occur and cause harm. By integrating advanced technologies, expert personnel, and structured processes, TDR systems deliver a proactive approach to safeguarding networks, data, and applications.
At their core, threat detection and response systems focus on two key functions,
Threat Detection, which identifies anomalies, patterns, or indicators of compromise (IoCs), and
Threat Response, which neutralizes these risks in real-time.
Utilizing modern technologies like machine learning (ML), and artificial intelligence (AI), TDR systems enhance their ability to detect even the most sophisticated threats.
Some of the key components of an effective cybersecurity strategy include real-time monitoring, automated incident response, and multi-layered security that spans network, endpoint, cloud, and application defenses.
Seamless integration with tools like Security Information and Event Management (SIEM) systems ensures a cohesive cybersecurity ecosystem, while dynamic threat hunting and user behavior analytics (UBA) further strengthen defenses against hidden risks and insider threats.
Benefits of Threat Detection and Response Systems
Effective threat detection and response strategies play a crucial role in enhancing organizations’ resilience against cyber threats and minimizing the impact of potential breaches. Some of the benefits of TDR systems are,
1. Secure Sensitive Information
Data is a vital asset for major businesses. The most suitable threat detection and response tools and procedures help security teams to identify bad actors before they gain access to sensitive data which reduces the likelihood that the information will be public or be sold on the dark web.
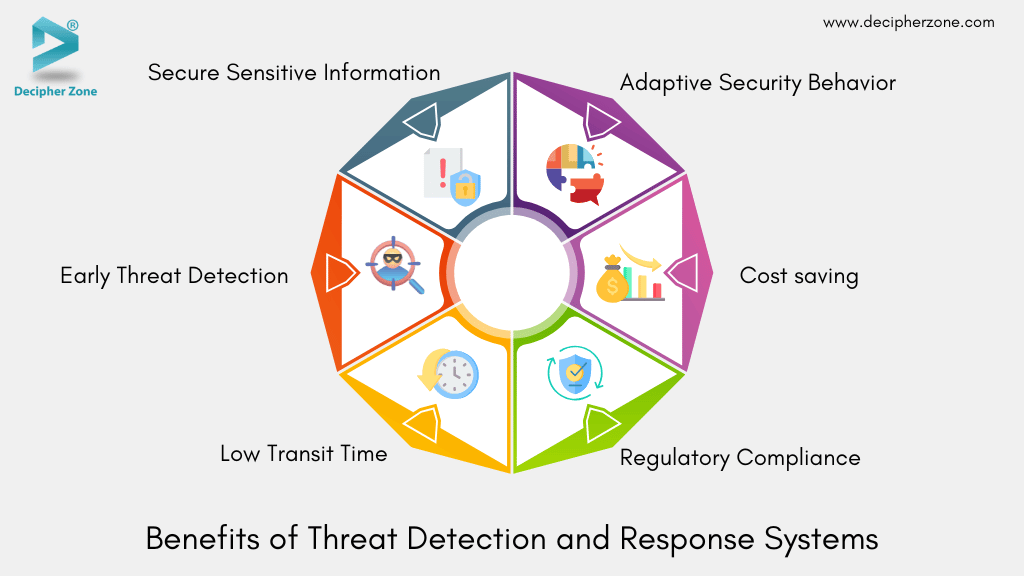
2. Early Threat Detection
Stopping cyber threats early, before they turn into major security breaches, is one of the best ways to minimize damage and disruption. Modern threat detection and response tools, combined with a skilled team, make this possible.
Security Operations Centres (SOCs) equipped with these tools are much more likely to catch threats early when they are simpler and less costly to handle.
3. Low Transit Time
The most harmful cyberattacks often happen when attackers remain hidden in a system for a long time, causing damage without being noticed. Reducing this transit time is crucial to minimizing the harm they can cause.
Threat detection and response methods, such as threat hunting help SOCs quickly identify and stop these attackers which reduces the impact and protects the organization.
4. Regulatory Compliance
Many countries and regions have implemented strict privacy laws that require organizations to maintain strong data security and have clear plans for handling security incidents.
Failure to comply with these regulations can lead to heavy penalties. The suited threat detection and response program not only strengthens data protection but also helps organizations meet these legal requirements, ensuring compliance and avoiding fines.
5. Cost saving
By spotting threats early and acting quickly, businesses can stop attacks before they get worse, saving money and reducing the overall impact of security incidents as cyberattacks can cost a lot of money in the form of ransom, fines, or covering recovery efforts.
6. Adaptive Security Behavior
The adaptive nature of threat detection and response systems helps identify new and emerging threats, showing how attackers might break into a company’s digital systems. With this approach, SOCs can strengthen the business defenses and stop future attacks before they happen.
How do Threat Detection and Response Systems Work?
Threat detection and response systems help businesses identify and mitigate cyber threats. Many businesses establish a SOC that focuses on enhancing cybersecurity, thwarting attacks, and addressing potential threats.
These teams, whether composed of in-house experts or outsourced professionals, operate around the clock to monitor systems, pinpoint emerging risks, and patch vulnerabilities. Here is how the process works,
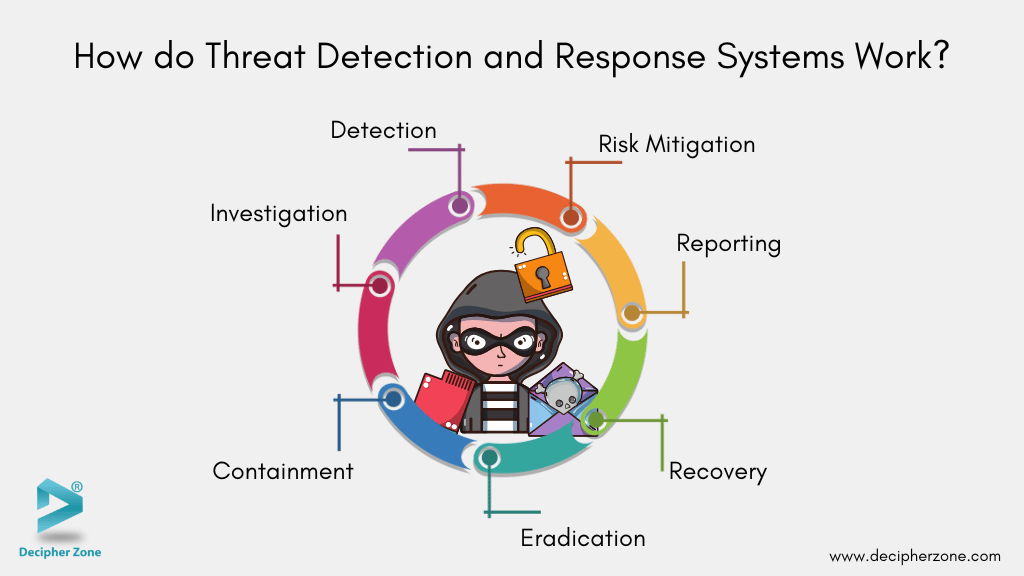
1. Detection
Security tools play a crucial role in monitoring various aspects, including networks, endpoints, user behavior, and cloud systems. They employ techniques like behavior analysis, machine learning, and threat intelligence to identify potential problems, even those that are often difficult to detect. Threat hunting actively looks for concealed threats that help reveal sophisticated attacks that could otherwise go unnoticed.
2. Investigation
When a risk is identified, the SOC team employs sophisticated tools to verify if it poses a genuine threat. They investigate the incident to understand what transpired, how it happened, and which systems or data have been impacted.
3. Containment
To prevent the speed of the treatment, the team promptly isolates any affected device, accounts, or systems. This proactive measure prevents the attack from extending its impact to other areas within the organization.
4. Eradication
The root cause of the attack has been pinpointed and completely eliminated. The vulnerabilities that enabled the threat have been addressed to ensure that a similar attack doesn’t occur again.
5. Recovery
After the threat has been dealt with, the team works to restore normal operations, carefully reconnecting any isolated systems to ensure safety.
6. Reporting
A detailed report is drafted to outline the incident, detailing how it was addressed and the insights gained from the experience. This report is then shared with the leadership to improve security protocols for the future.
7. Risk Mitigation
Building on the lessons learned from the incident, the team improved processes, tools, and systems to strengthen defenses and lower the likelihood of facing similar threats in the future.
By integrating advanced technologies with human expertise, threat detection and response systems provide continuous protection, enable swift action against risks, and promote ongoing enhancements to shield organizations from evolving cyber threats.
What Threats Does TDR Identify & Prevent?
Security teams have traditionally focused on protecting networks and endpoints, but as cyber threats have grown more sophisticated and frequent, their approaches have had to evolve.
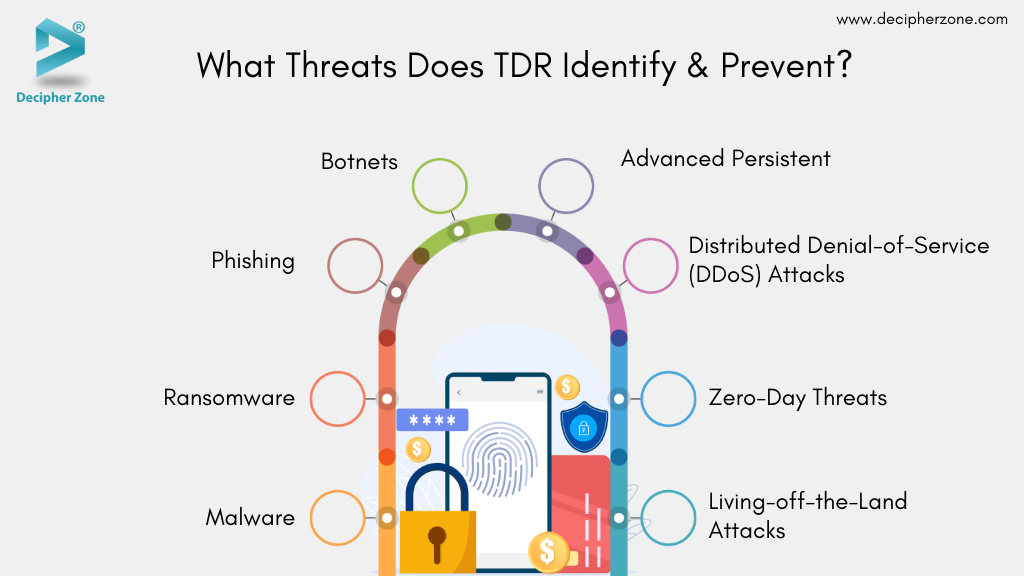
TDR tools provide improved visibility into complex attacks which allow faster action to minimize disruptions and risks. These tools are designed to detect and address a wide range of threats, including:
-
Malware: Malicious software like spyware and Trojans are created to infect systems and steal sensitive data.
-
Ransomware: A leading cyber threat where attackers encrypt and exfiltrate critical data, demanding payment to decrypt it and avoid public disclosure or sale.
-
Phishing: A common tactic in social engineering involves deceiving users into revealing their credentials or sensitive information. Attackers then exploit this information to install malware or gain unauthorized access to systems.
-
Distributed Denial-of-Service (DDoS) Attacks: Imagine a digital chaos where massive waves of traffic flood the system, overwhelming servers until they buckle and crash. This deluge of activity not only brings services to a standstill but creates a ripple effect, leaving users frustrated and disconnected.
-
Botnets: Networks of compromised devices that attackers leverage for a range of malicious activities. These may include sending out spam, launching DDoS attacks, or stealing sensitive data.
-
Advanced Persistent: Long-term cyberattacks where attackers infiltrate networks to steal sensitive data over extended periods.
-
Zero-Day Threats: Exploits targeting software or hardware vulnerabilities that are unknown to developers and unpatched.
-
Living-off-the-Land Attacks: Attacks where legitimate tools and resources within a network are abused to compromise systems stealthily.
The pace at which attackers operate is staggering. A crucial security metric is known as breakout time. The time it takes for an attacker to move laterally within a network has significantly decreased in recent years, from 98 minutes down to just 62 minutes, according to recent reports from CrowdStrike.
Features of Threat Detection and Response Systems
Threat detection and response system solutions are designed to enhance the speed and accuracy of detecting threats and responses to minimize the damages done by security incidents. Some of the features of threat detection and response systems are:
1. Real-Time Monitoring
TDR system solutions provide ongoing monitoring of the networks, systems, and endpoints leaving any point unattended and detecting any suspicious activities before they take place which reduces the time frame between when the emergence of a threat begins and detects. This not only ensures no gaps are left unprotected but also offers a full, extensive view of the infrastructure.
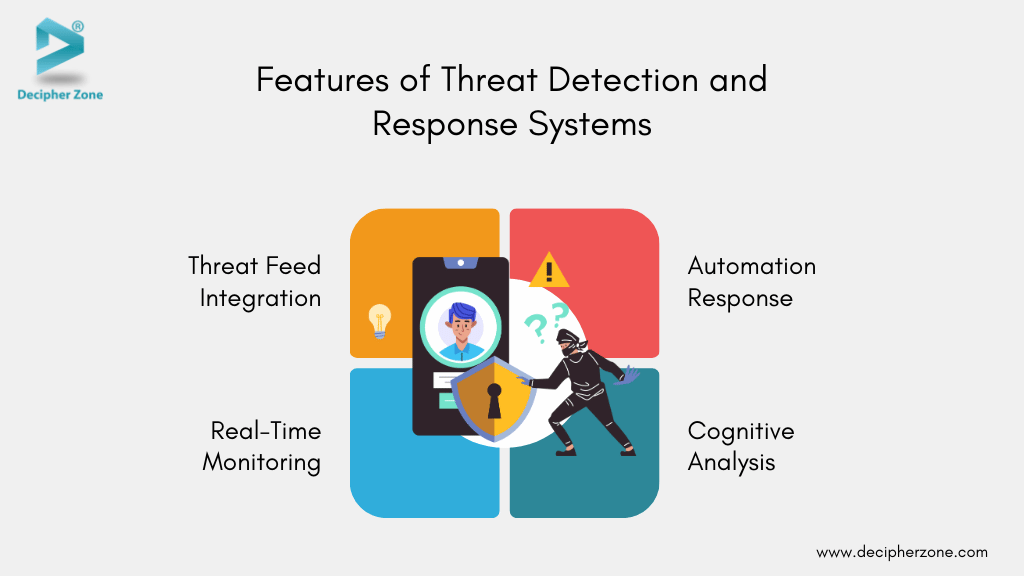
2. Threat Feed Integration
Threat detection and response systems are designed to continuously refresh and update the latest data on emerging threats, vulnerabilities, and the evolving tactics of cybercriminals.
With the security researchers, global attack patterns, and government advisories these feeds are sourced. By incorporating this information, TDR systems are able to identify new malware signatures, phishing strategies, and indicators of compromise.
3. Cognitive Analysis
Utilizing cognitive analysis to identify activities that deviate from normal user or system behavior, which could signal a potential security threat.
TDR systems establish a baseline for typical activities such as login patterns, system resource usage, and the method a user employs to access the systems. This approach is particularly effective in spotting insider threats or compromised accounts that may otherwise go unnoticed.
4. Automation Response
TDR systems incorporate automated capabilities that can neutralize a threat as soon as it’s identified. These automated responses may involve isolating compromised devices, blocking specific IP addresses associated with malicious hosts, or shutting down infected processes. The quicker response reduces the window and decreases the opportunity for an intruder.
Best Practices in Threat Detection and Response Systems
The most effective way to maximize Threat Detection and Response (TDR) systems, businesses should adopt a strategic and multi-layered approach. Here are the key best practices that help create robust defense:
1. Implement Advanced Detection Techniques
Use strategies like anomaly detection, behavior analysis, and sandboxing to identify threats that can slip past traditional security measures. These approaches offer deeper insights into stealthy attacks and boost your threat detection capabilities.
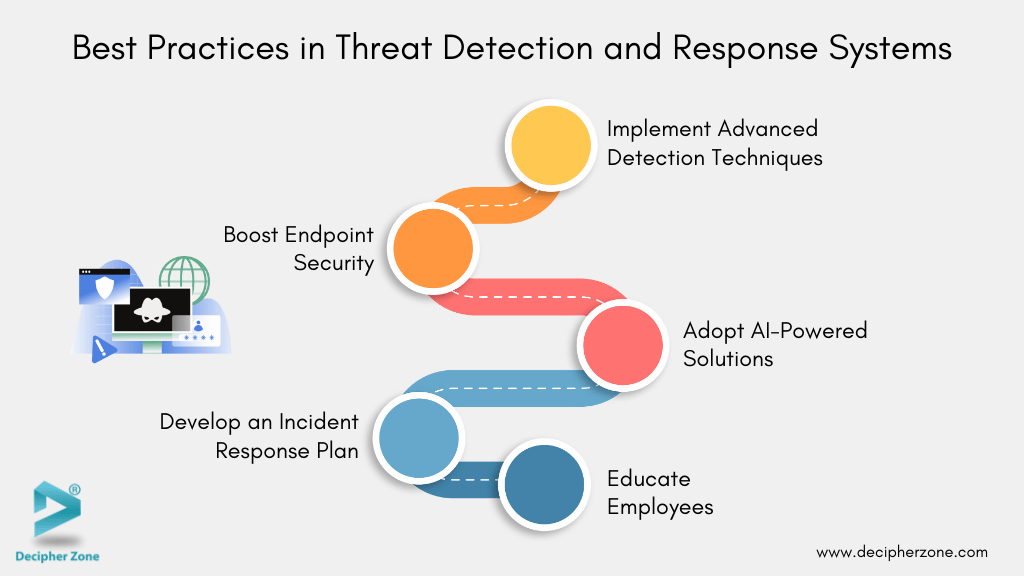
2. Boost Endpoint Security
Deploy advanced endpoint security protection solutions and minimize the risk of breaches, it’s essential to implement it regularly update systems, and utilize host-based intrusion prevention systems (HIPS). Adopting these measures will significantly enhance your security posture.
3. Develop an Incident Response Plan
Create and regularly assess a detailed incident response plan. Clearly define the roles and responsibilities of each team member, detail the steps for containment and recovery, and ensure adherence to relevant regulations. This level of preparation allows teams to respond effectively during critical situations.
4. Educate Employees
Provide employees with training on the best practices for cyberthreats such as recognizing phishing attempts and using strong passwords. Regular training sessions encourage a culture of security awareness, empowering staff to identify and report potential threats effectively.
5. Adopt AI-Powered Solutions
Use AI-driven tools such as SIEM and XDR solutions to enhance alert correlation, accelerate threat detection, and streamline threat mitigation. Advanced AI tools can disrupt ongoing attacks and provide actionable insights for SOC teams.
Common Types of Threat Detection and Response Systems
Organizations need to have a variety of adaptable and capable systems to address advanced threats. The following section explains the types of threat detection and response systems that counter evolving threats effectively:
1. Network Detection and Response (NDR)
NDR solutions focus on monitoring and analyzing network traffic to identify suspicious activities or potential breaches. By utilizing advanced technologies like artificial intelligence (AI), machine learning (ML), and behavior-based detection, network detection and response can uncover threats that bypass traditional signature-based methods.
These tools provide deep visibility into network infrastructure which helps businesses to respond proactively to anomalies or unauthorized access attempts.
2. Endpoint Detection and Response (EDR)
EDR continuously monitors endpoint devices like laptops, servers, and workstations for signs of malicious activity. These tools collect data from endpoints, analyze it for potential threats, and trigger automated responses based on preconfigured rules.
This approach enhances perimeter security and provides actionable insights to protect devices against malware, ransomware, and other endpoint-targeted attacks.
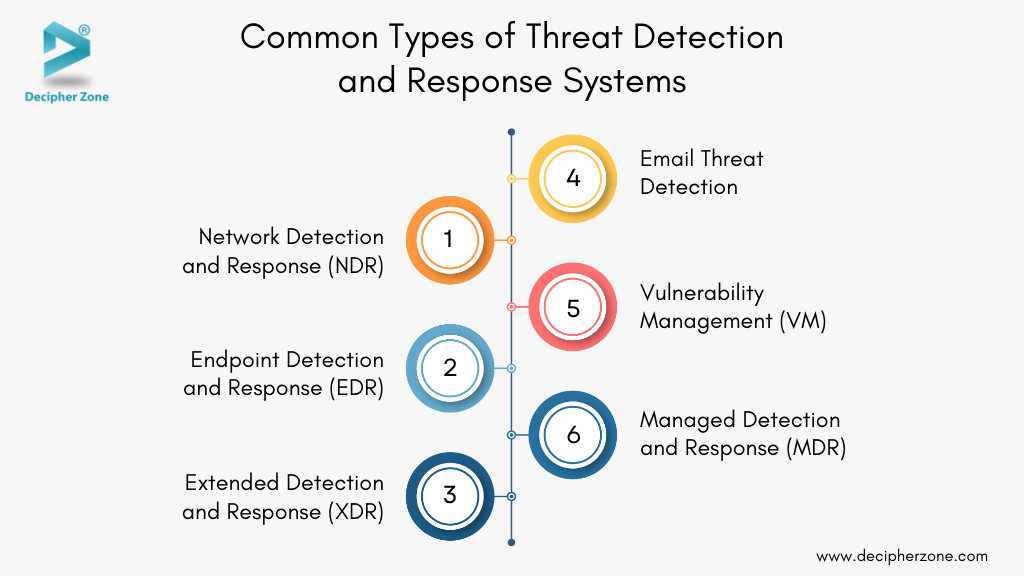
3. Extended Detection and Response (XDR)
A unified security solution designed for comprehensive protection across multiple domains. Extended Detection and Response (XDR) consolidates data from endpoints, networks, cloud environments, and emails to detect, prioritize, and remediate threats more effectively.
By prioritizing a centralized view and automating responses, XDR enables the security operations team to manage threats with greater speed and precision.
4. Email Threat Detection
Email threat detection tools can operate as standalone solutions or as a part of integrated platforms like XDR. These tools scan and analyze email traffic to identify malicious links, phishing attempts, and malware-laden attachments.
This not only quarantines harmful emails but also uses advanced algorithms to prevent threats from reaching inboxes which ensures robust email security.
5. Vulnerability Management (VM)
Vulnerability management is all about identifying and addressing weaknesses in an organization’s IT systems and infrastructure. By scanning known and emerging vulnerabilities, VM tools help prioritize remediation efforts according to their risk levels.
Conducting regular assessments ensures that security patches are applied promptly, reducing the likelihood of exploitation by cybercriminals.
7. Managed Detection and Response (MDR)
Managed detection and Response (MDR) services merge human expertise with advanced security tools to monitor, identify, and respond to threats. MDR provides use threat intelligence and conduct incidents. This service is particularly beneficial for organizations that require around-the-clock monitoring and rapid incident resolution without maintaining an in-house security team.
Methods of Threat Detection
Many techniques can help identify and respond to potential security threats and harmful activities in the IT environment. These techniques fall into four main categories of threat detection:
|
Methods of Threat Detection |
Meaning |
|
Signature-based Detection |
Comparing observed data such as network traffic patterns, against established rules or known patterns of malicious activity is an effective way to spot threats, particularly for identifying known malware and attack techniques. This approach may fall short when it comes to recognizing novel or polymorphic threats that don’t align with existing signatures. |
|
Anomaly-Based Detection |
This process identifies deviations from typical behavior or baseline patterns within the IT environment, which may signal a potential security threat. Anomaly threat detection management has the ability to reveal previously unknown threats, insider threats, and zero-day attacks. As the complexity of environments increases and general usage patterns evolve over time, it may also lead to false positives. |
|
Behavior-Based Detection |
This kind of process involves monitoring for potential threats by identifying lateral movement, privilege escalation, and data exfiltration which concerns that might slip past other security measures. Behavior-based detection relies on analytics and a thorough understanding of the usual behavior of users, applications, and systems. |
|
Threat Intelligence-Based Detection |
Incorporating threat intelligence into detection processes not only bolsters existing methods but also enriches security alerts with vital contextual information, facilitating proactive threat hunting. External feeds and indicators of compromise can help identify known malicious entities, allowing for proactive blocking of threats such as specific IP addresses, domains, or file hashes linked to cyber dangers. |
Threat Detection and Response Systems Challenges
Threat detection involves identifying potential threats, but this process comes with several challenges. These challenges arise from the difficulty in spotting threats, the changing nature of risks, and the need for accurate, real-time analysis. Navigating this process requires careful attention to these issues. Here are some challenges:
1. Advanced and Expanding Threat Environment
Attackers are always adapting their tactics, finding new ways to slip through defenses and evade detection. It is a dynamic game of cat and mouse that keeps security professionals on their toes.
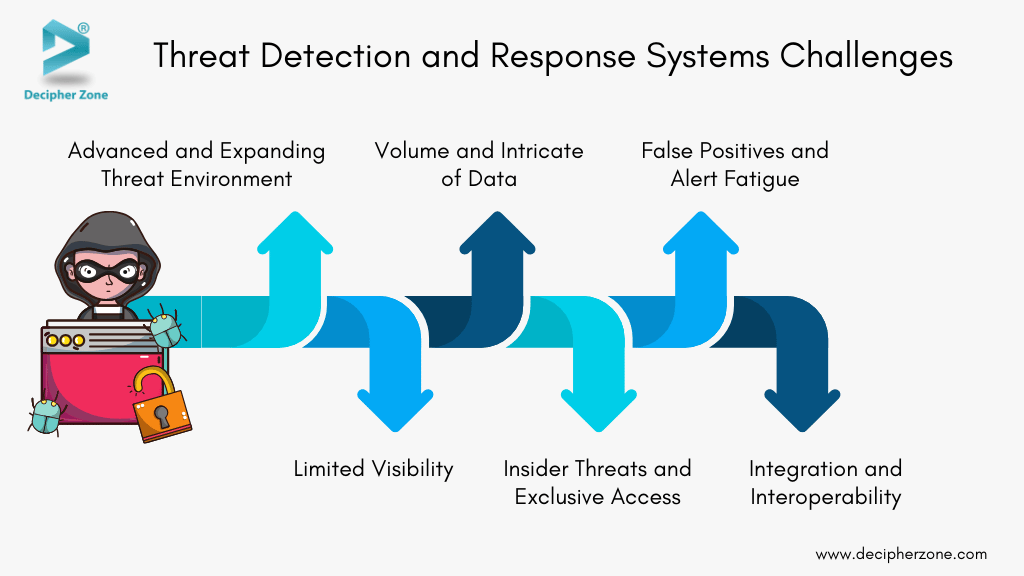
2. Volume and Intricate of Data
Analyzing huge quantities of information from a variety of sources in real time is no small feat. It requires a keen eye and robust strategies to make sense of the complexities involved.
3. False Positives and Alert Fatigue
Sifting through countless notifications to identify real security threats requires significant time and valuable resources. It is a daunting task but distinguishing the genuine risks from the background noise is crucial for maintaining a strong defense.
3. Limited Visibility
Blind spots, decentralized infrastructure, legacy systems, or shadow IT are caused by incomplete visibility into the environment which makes detecting and responding to security threats effectively challenging. Sometimes security teams may lack understanding of the significance of events they detect.
4. Insider Threats and Exclusive Access
Ensuring that privileged users don’t misuse their access is crucial for maintaining security. By closely monitoring user behavior, upholding the principle of least privilege, and putting in place strong access controls, a safer environment can be created.
5. Integration and Interoperability
Tools and technologies often function in isolation which leads to fragmented threat detection and response. This disconnection makes it challenging to get a comprehensive view of potential threats. To bridge these gaps and achieve interoperability among various solutions, businesses must invest considerate time and effort.
Final Thoughts
Threat detection and response systems have become crucial pillars of effective cybersecurity strategies. These elements allow businesses to not only identify potential cyber threats but also to fend them off and respond promptly in real time.
By analyzing network traffic patterns with threat detection and response tools, you can spot suspicious activities before they escalate into serious issues, promptly alerting the system to respond.
Incorporating these tools offers deep insights and enhances overall network performance, ensuring the defenses are robust and ready for anything the cyber world throws your way.

Decipher Zone can help you develop top-notch solutions integrating threat detection and response tools to safeguard user information and your organization’s data.
Our team of experts can alleviate the challenges you might face and curate considering your unique requirements. Partner with us to upscale your business with robust cybersecurity strategies, advanced technologies, and a seamless integration process.
FAQs
-
What is threat detection and response?
Threat detection and response systems are essentially helping organizations identify and mitigate malicious activities before they occur and cause harm. By integrating advanced technologies, expert personnel, and structured processes, TDR systems deliver a proactive approach to safeguarding networks, data, and applications.
-
What are the benefits of implementing TDR in the business?
Some of the benefits of TDR systems are Secure Sensitive Information, Early Threat Detection, Low Transit Time, Regulatory Compliance, Cost saving, and Adaptive Security Behavior.
-
What are the types of threat detection and response systems?
There are mainly six types of threat detection and response systems, such as Network Detection and Response (NDR), Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Email Threat Detection, Vulnerability Management (VM), and Managed Detection and Response (MDR).

