Automation incident response software is a vital ally in the quest for stronger cybersecurity, encouraging businesses to detect, contain, and resolve security incidents in real-time. If you’re building a safety guard around your assets and looking for all the information. You have come to the right page! This article covers from meaning, process, why to invest, core features, and practical applications of automated incident response software.
Cyber threats are severe. From data breaches to ransomware attacks, businesses face an ever-growing risk that demands rapid and effective response strategies. The challenges? Security teams are often inundated with thousands of alerts daily, making it nearly impossible to investigate each threat manually. Delayed responses can lead to financial losses, reputational damage, and regulatory consequences.
Automation incident response software plays a crucial role in enhancing cybersecurity measures for businesses. By utilizing automation, organizations can effectively detect, contain, and address security incidents in real-time.
This capability significantly reduces response times and minimizes potential damage. Automated solutions encourage security teams to filter through numerous alerts, allowing them to differentiate between genuine threats and false positives. As a result, teams can take timely and precise actions when faced with critical security challenges.
But how exactly does automated incident response work, and why is it becoming a necessity? This blog discusses how automation incident response software transforms cybersecurity, its key benefits, and how organizations can implement it effectively to stay ahead of evolving threats.
Whether you’re just starting your automation incident response journey or looking to improve existing processes, this article provides actionable insights for success.
Read: Customer Service Automation
What is Incident Response Software?
Incident Response Software (IRS) is a comprehensive set of tools and methodology for assisting organizations in detecting, addressing, and recovering from cybersecurity incidents. Its primary goal is to minimize damage and facilitate a swift restoration of operations.
Incident response automation encompasses a range of activities designed to streamline the response process. These include:
-
Identifying security incidents in cloud environments,
-
Determining attack vectors, which are the pathways through which threats penetrate systems,
-
Evaluating the urgency and potential impact of incidents,
-
Gathering and analyzing relevant data to understand the situation,
-
Implementing resolution steps to mitigate the incident,
-
Documenting the incident and the steps taken for remediation.
By automating these processes, organizations can enhance their incident response capabilities and improve overall security resilience.
How does the Incident Response Software System Work?
Incident response is a structured approach to identifying, managing, and mitigating cybersecurity incidents to minimize damage and prevent future breaches. Most organizations follow standardized frameworks like those developed by the National Institute of Standards and Technology (NIST) and the SANS Institute, which outline key phases of an effective response.
Here’s how the process works:
Phase1: Preparation
Before an incident even occurs, organizations must establish a Cyber Security Incident Response Team (CSIRT) and develop a robust incident response plan. A well-prepared team can detect and neutralize threats faster, reducing potential damage.
This includes:
-
Conducting risk assessments to identify vulnerabilities,
-
Implementing security tools and monitoring systems,
-
Running “wargame” simulations to test response strategies,
-
Establishing communication protocols for swift action during a breach.
Phase 2: Detection and Analysis
The security team continuously monitors logs, firewalls, intrusion detection systems (IDS), endpoint protection platforms (EPP), and SIEM (Security Information and Event Management) solutions to detect potential threats. Early detection prevents small incidents from escalating into full-blown breaches.
The key tasks include:
-
Identifying unusual activity or security alerts,
-
Filtering out false positives to focus on real threats,
-
Classifying incidents based on severity and impact,
-
Notifying the relevant stakeholders for immediate response.
Read: Network Security Management Software
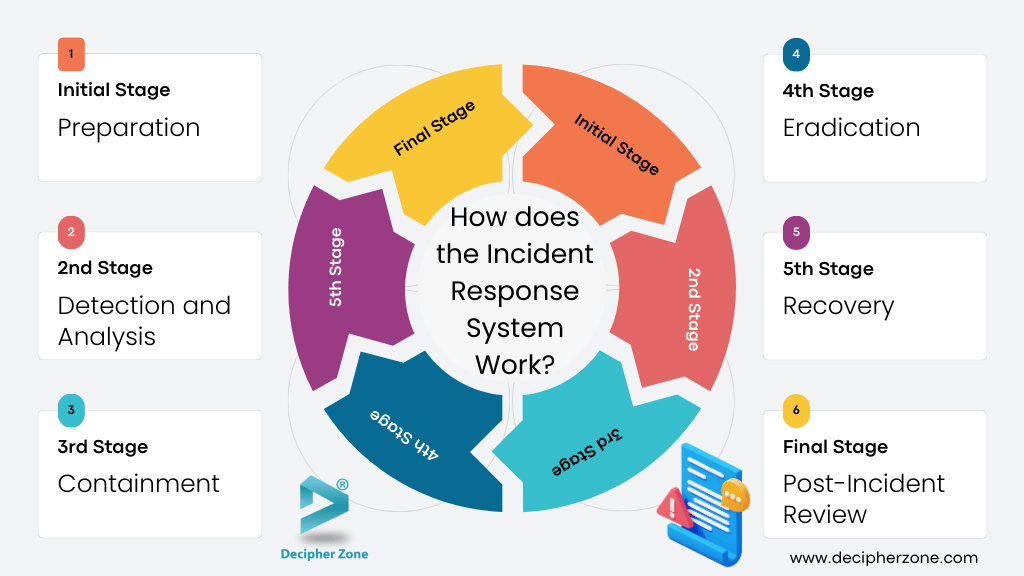
Phase 3: Containment
Once a threat is identified, the focus shifts to preventing further damage. Containment limits the impact of an attack and prevents further compromise. Containment strategies are categorized as:
-
Short-term Containment: Immediately isolating affected systems or users to stop the spread of malware or unauthorized access.
-
Long-term Containment: Implementing additional security measures, such as network segmentation or firewall adjustments, to prevent recurrence.
-
Forensic Backup: Securely storing affected data for analysis while preserving evidence for future investigation.
Phase 4: Eradication
With the threat contained, the CSIRT works on completely removing it from the network. Simply stopping an attack isn’t enough—full remediation ensures it doesn’t return. This may involve:
-
Eliminating malware, malicious scripts, or unauthorized accounts,
-
Patching vulnerabilities exploited in the attack,
-
Strengthening security policies to prevent similar threats.
Phase 5: Recovery
Once eradication is complete, organizations begin restoring affected systems and resuming normal operations. Proper recovery ensures business continuity with minimal disruption. Key activities include:
-
Restoring data from secure backups,
-
Rebuilding or reconfiguring compromised systems,
-
Conducting security audits to ensure no remnants of the attacks remain.
Phase 6: Post-Incident Review
Every incident provides an opportunity to improve security. Continuous learning helps strengthen defenses and reduces the risk of future attacks. The CSIRT conducts a detailed review to answer key questions:
-
What was the root cause of the incident?
-
Were the responses efficient in terms of effort and effectiveness?
-
How can security policies, tools, or training be improved?
-
Do law enforcement or regulatory bodies need to be informed?
Key Features to Consider While Developing an Incident Response Software
Incident response automation software offers a comprehensive range of features designed to streamline the entire incident response lifecycle. Here is the list:
-
Incident Detection & Triage
-
Automated Incident Analysis
-
Automated Incident Response & Remediation
-
Incident Reporting & Documentation
-
Collaboration & Workflow Management
-
Incident Response Playbook Management
1. Incident Detection & Triage
These tools rapidly detect and prioritize security incidents, leveraging advanced analytics, threat intelligence, and integrated security solutions. This allows security teams to focus on the most critical threats.
Artificial intelligence and machine learning algorithms allow the software to continuously monitor for anomalies, identify potential indicators of compromise, and trigger immediate alerts.
2. Automated Incident Analysis
Leveraging Artificial Intelligence algorithms, incident response software automates the analysis of security incidents to quickly identify the root cause, evaluate the scope of the breach, and determine the appropriate response actions.
This enhances the ability to correlate data from multiple sources, for example, security logs, network traffic, and vulnerability scans, to provide a robust contextual understanding of the incident.
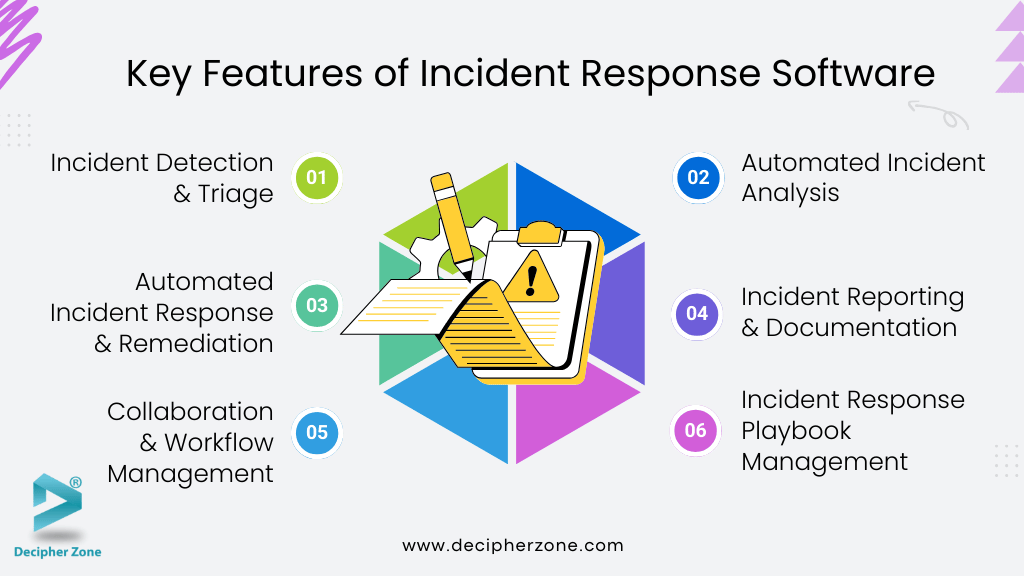
3. Automated Incident Response & Remediation
Once an incident has been detected, these tools can automatically initiate predefined response procedures, including isolating affected systems, implementing security controls, and executing remediation tasks—all without the need for human intervention. This swift, automated response can significantly shorten the time it takes to contain and mitigate the impact of a security incident.
4. Incident Reporting & Documentation
Incident response automation software delivers comprehensive reports and documentation, which provides a detailed record of the incident response process. These reports mostly include information on the incident’s timeline, the actions taken, the root cause analysis, and the overall impact. This enables security teams to demonstrate the effectiveness and adherence to industry best practices.
5. Collaboration & Workflow Management
These tools include features that allow cross-functional collaboration that enabling security teams to coordinate with IT, legal, and other relevant stakeholders during the incident response process. This can also incorporate workflow management capabilities to streamline the execution of response actions, ensuring seamless communication and task allocation within the organization.
6. Incident Response Playbook Management
Incident response automation software enables businesses to design and manage a customized incident response playbook that outlines the precise steps to be taken in response to different types of security incidents. These playbooks are readily updated and deployed across the organization, ensuring a uniform and well-defined response approach.
Read: Cybersecurity Trends
Top 7 Benefits of Investing in Incident Response Software Development
Automation systems for incident response provide significant advantages by scrutinizing and leveraging numerous benefits of telemetry, security, and health data produced by different network, system, and security components.
Below, we are listing benefits for organizations implementing a comprehensive automated incident response program.
1. Automate Manual Security Processes
Automated incident response allows security teams to focus on security events by streamlining manual tasks. By automating alert notifications, investigations, triage, ticket generation, and report creation, analysts can dedicate their skills to more critical areas.
2. More Efficient Security Operations
Automation enhances incident detection and response by providing greater proactively, consistency, and speed. Analysts can prioritize stopping attacks rather than manually documenting threats, leading to improved efficiency and quicker resolution in security operations.
3. Generate Critical Insights in Real-Time
An automated incident response platform provides a centralized dashboard for security teams to prioritize and manage alerts effectively. Notifications can be enriched from various security intelligence sources, enhancing insights into threats and improving response efforts.
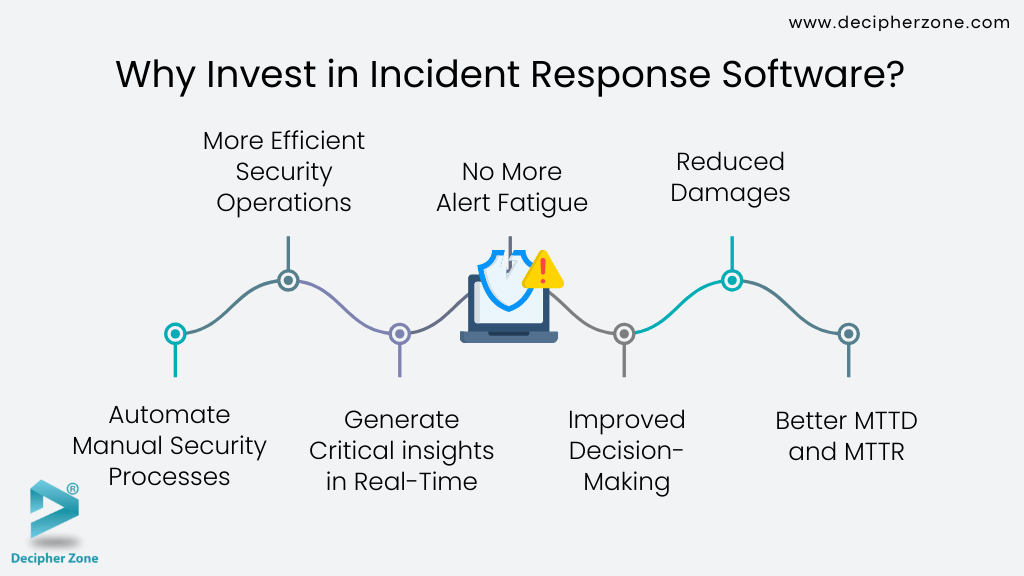
4. No More Alert Fatigue
Many organizations face an overwhelming number of alerts from security tools, requiring analysts to manually review each one to identify genuine threats. While manageable with fewer alerts, this process can consume days for SOC teams handling daily alerts, leading to alert fatigue.
This fatigue often results in real threats being overlooked, increasing vulnerability. Automated incident elements from alert analysis, allowing security teams to analyze and remediate more threats, thus enhancing business security.
5. Improved Decision-Making
An automated incident response plan outlines the specific roles of each team member during an incident. This not only accelerates the response process but also makes sure that the right decision-makers are actively involved when a threat arises.
6. Reduced Damages
Automated incident response allows the organization to respond more effectively and swiftly during an actual cyberattack, helping to minimize its impact on your business.
7. Better MTTD and MTTR
MTTD (Mean Time to Detect) is the average amount of time it takes to identify a security issue or event. On the other hand, MTTR (Mean Time to Respond) is the average amount of time needed to mitigate and control the threat.
By detecting real threats from false positives, automated incident response enables companies to identify and address risks more quickly.
Read: Guide to Virtual Private Networks (VPNs)
Practical Applications of Automated Incident Response (Use Cases)
Cybersecurity doesn't wait, and neither should your response. By eliminating manual bottlenecks, automated incident systems enhance speed, accuracy, and efficiency in handling security incidents.
From blocking ransomware in real time to preventing unauthorized access, automated response is revolutionizing cybersecurity. Here are some of the most impactful applications and use cases:
-
Real-Time Threat Detection
AI algorithms continuously monitor network traffic and system logs to spot unusual behavior that could indicate potential security threats. By leveraging machine learning and pattern recognition, AI can proactively identify emerging threats, allowing for swift responses and effective measures to protect organizational assets and maintain data integrity.
-
Automated Alert Prioritization
AI effectively categorizes and prioritizes security alerts by evaluating their severity and potential impact on the organization, utilizing advanced algorithms to ensure a comprehensive analysis.
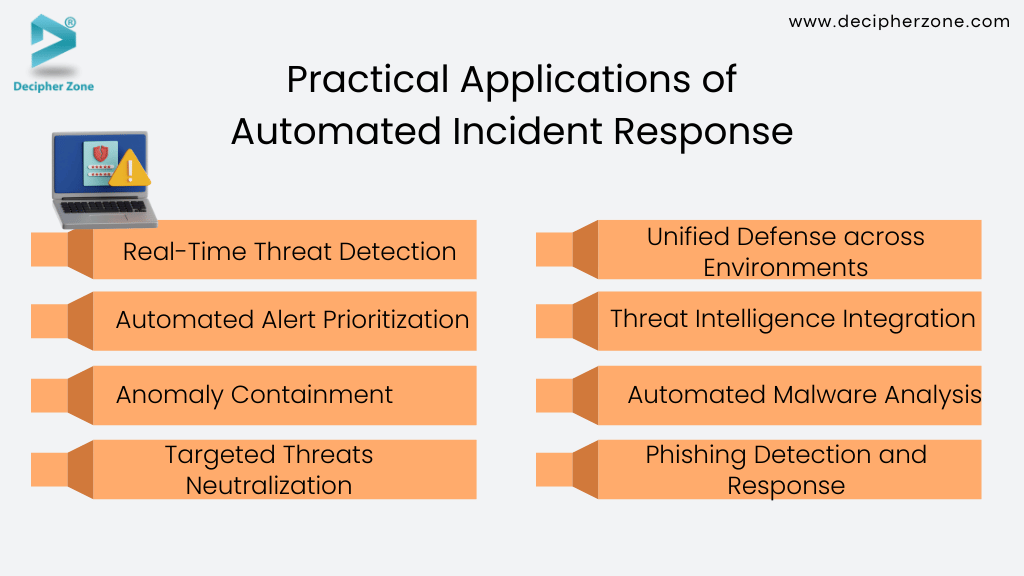
This approach allows security teams to prioritize their efforts, focusing first on addressing the most significant threats and vulnerabilities. AI-powered alert prioritization enhances overall incident response effectiveness and resilience against cyber threats by optimizing resource allocation and response time.
-
Anomaly Containment
By utilizing advanced anomaly detection techniques, the system quickly identifies and isolates unusual activities, such as unexpected data access or spikes in data transfer, by measuring them against established standards. This proactive approach effectively cuts off potential threats, reducing the risk of data breaches or insider incidents and protecting the organization's assets.
-
Targeted Threats Neutralization
AI utilizes continuous scanning capabilities to proactively disrupt the activities of cyber adversaries. By detecting signs of hidden threats, such as unusual network communication, the system can identify suspicious patterns and take immediate action.
It intervenes promptly by shutting down malicious processes and securely compromised data points to prevent further harm and change cybersecurity defenses.
-
Unified Defense across Environments:
The AI system operates as a unified security framework, effectively connecting on-premises and cloud infrastructure to ensure a coordinated response to incidents throughout the organization.
By automatically enforcing security protocol, it contains and mitigates incidents while maintaining operational continuity across all platforms. This approach enhances the overall security posture and resilience of the organization.
-
Threat Intelligence Integration:
AI-powered systems seamlessly integrate and interpret threat intelligence feeds in real-time to identify arising threats and vulnerabilities. These system improve threat detection by continuously updating and correlating threat data, which enables proactive responses to evolving cybersecurity threats.
-
Automated Malware Analysis:
AI-driven malware analysis solutions automate the analysis of suspicious files and executables in order to detect malware signatures and behavior patterns. These technologies use ML algorithms to identify and classify malware rapidly and correctly, allowing for quick reaction and mitigation steps to guard against cyber attacks.
-
Phishing Detection and Response:
AI algorithms scrutinize various elements of emails, such as their content, attachments, and the behavior of the sender, to identify phishing attempts and thwart successful attacks.
By analyzing email attributes and patterns that signal potential phishing, AI significantly boosts detection accuracy. This allows for prompt responses, like quarantining harmful emails or warning users of potential threats.
Read: Cloud-Based Software Development
Final Thoughts
It’s essential to modernize your incident response strategy without delay. Begin by evaluating your existing incident response processes to pinpoint areas where automation could significantly enhance efficiency and effectiveness. Remember to:
-
Begin small and scale gradually,
-
Focus on regularizing processes before automating them,
-
Invest in appropriate training for the team,
-
Choose appropriate tools to integrate with your existing infrastructure.
-
Review frequently and update your automation playbooks.
Automation in incident response is a continuous journey rather than a single project. Whether you’re just starting your automation journey or looking to enhance your organization’s existing capabilities.

Decipher Zone, our team of cybersecurity experts, is well-equipped to help you implement tailored incident response solutions that align with your unique business needs. From consultation to development and deployment, we provide end-to-end support to ensure your system is secure, resilient, and future-ready. Get in touch with us and take the first step towards building a stronger, smarter cybersecurity strategy.
FAQs
-
What is incident response software?
Incident Response Software (IRS) is a comprehensive set of tools and methodology for assisting organizations in detecting, addressing, and recovering from cybersecurity incidents. Its primary goal is to minimize damage and facilitate a swift restoration of operations.
-
What are the benefits of automated incident response software?
There are several benefits of automated incident response software, including automated manual security processes, more efficient security operations, generate critical insights in real-time, no more alert fatigue, improved decision-making, reduced damages, and better MTTD and MTTR.
-
What is the Incident Response System Workflow?
Incident response is a structured approach to identifying, managing, and mitigating cybersecurity incidents to minimize damage and prevent future breaches. It typically follows six key phases:
-
Preparation- establishing policies, tools, and response plans.
-
Detection & Analysis- identification and analyzing potential threats.
-
Containment- isolating affected systems to prevent further damage.
-
Eradication- removing the threat from the environment.
-
Recovery- restoring systems and resuming normal operations.
-
Post Incident Review- analyzing the incident to improve future response.

